
Amazon.com: USB Defender | Data Blocker | Blocks Unwanted Data Transfers | Protects Smartphone & Tablets From Public Charging Stations | Hack Proof, 100% Guaranteed : Electronics

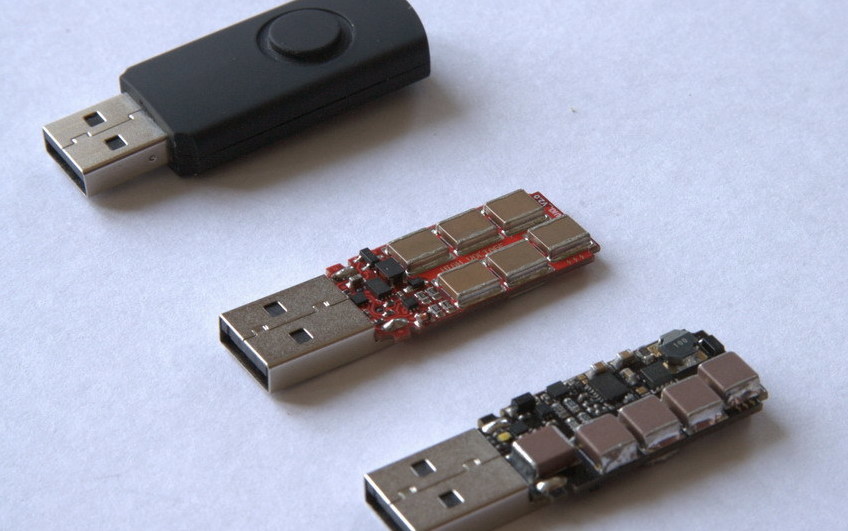
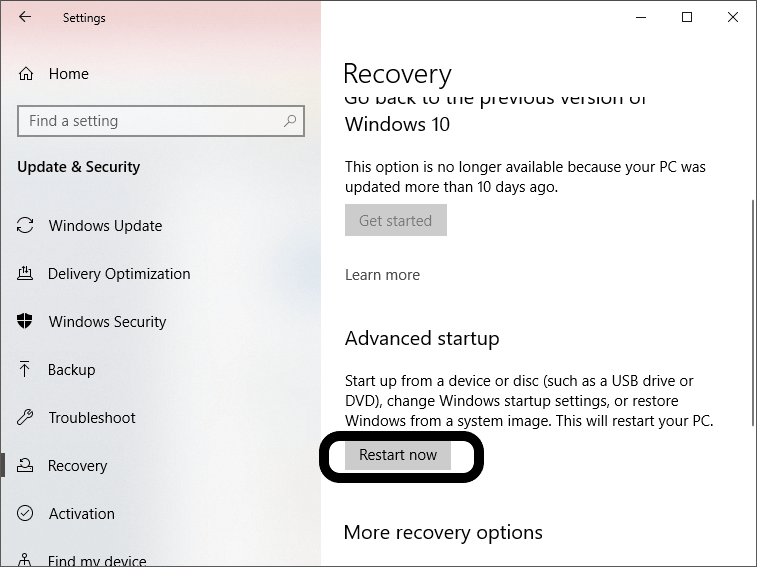
Hacking Windows 10: How to Break into Somebody's Computer Without a Password (Setting Up the Payload) « Null Byte :: WonderHowTo

/cdn.vox-cdn.com/uploads/chorus_asset/file/23949203/226141_rubberDucky.jpg)













/cdn.vox-cdn.com/uploads/chorus_asset/file/18993465/omg3_800x.jpg)





