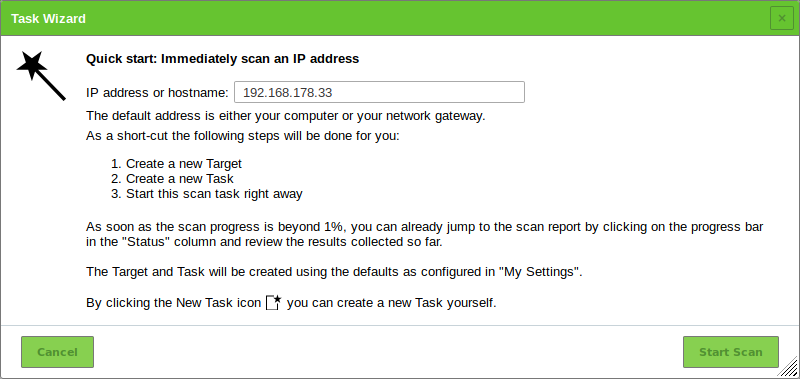
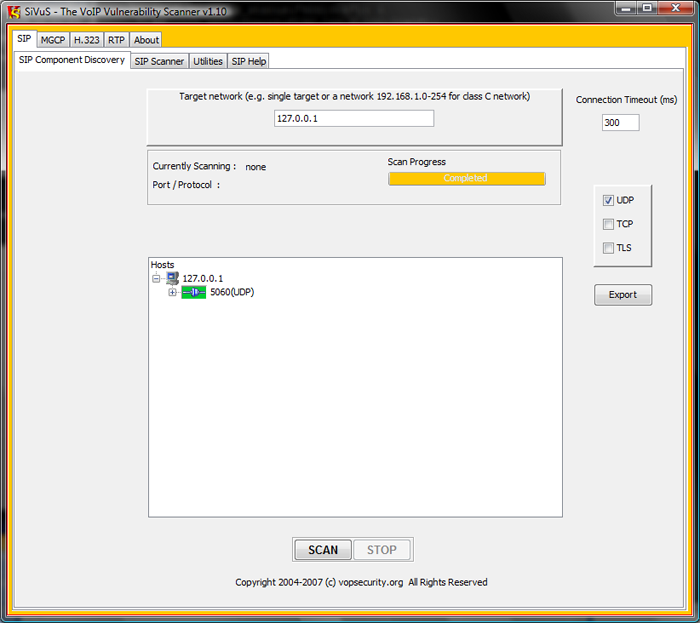
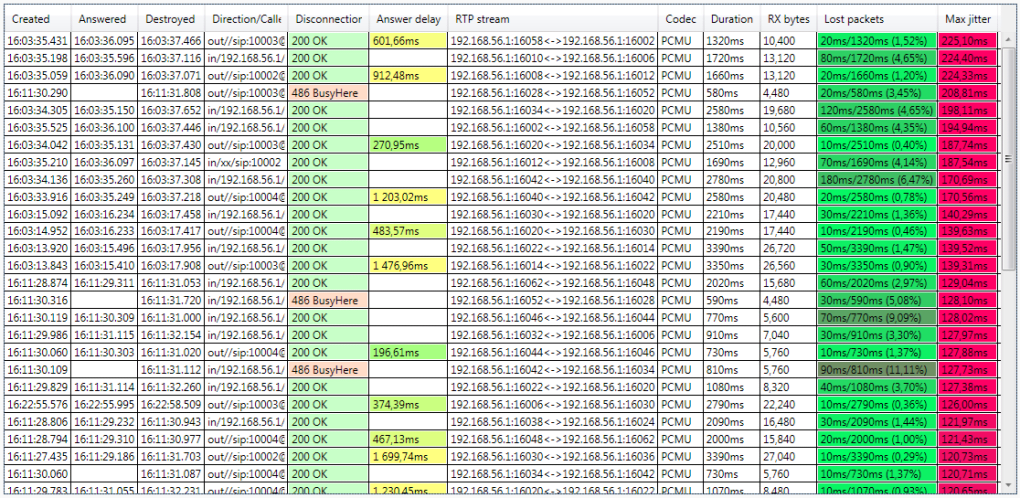
SIPVicious (Auditing SIP Based VoIP System) :: Tools - ToolWar | Information Security (InfoSec) Tools

Eyoyo EY-019W Wireless Barcode Scanner, Handheld 2.4G Wireless & USB Wired 2D Barcode Reader Support QR PDF417 Data Matrix Screen Scanning Auto Sensing for Warehouse Library Store,2D barcode scanner