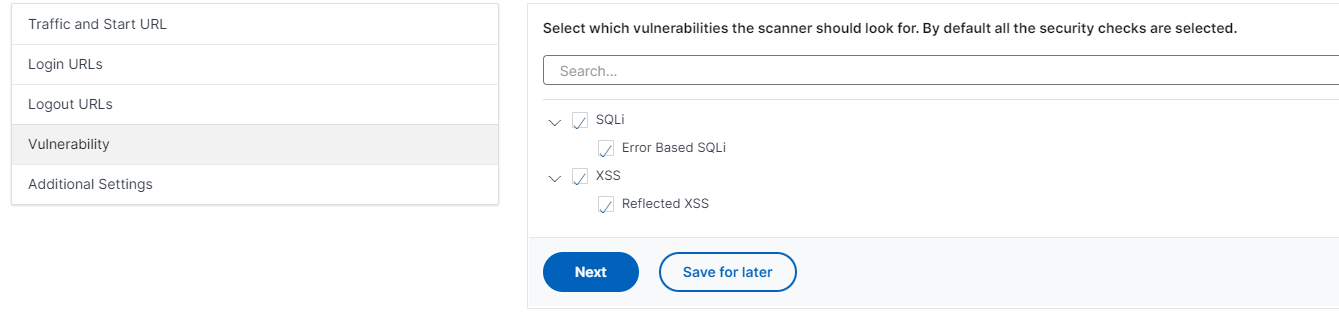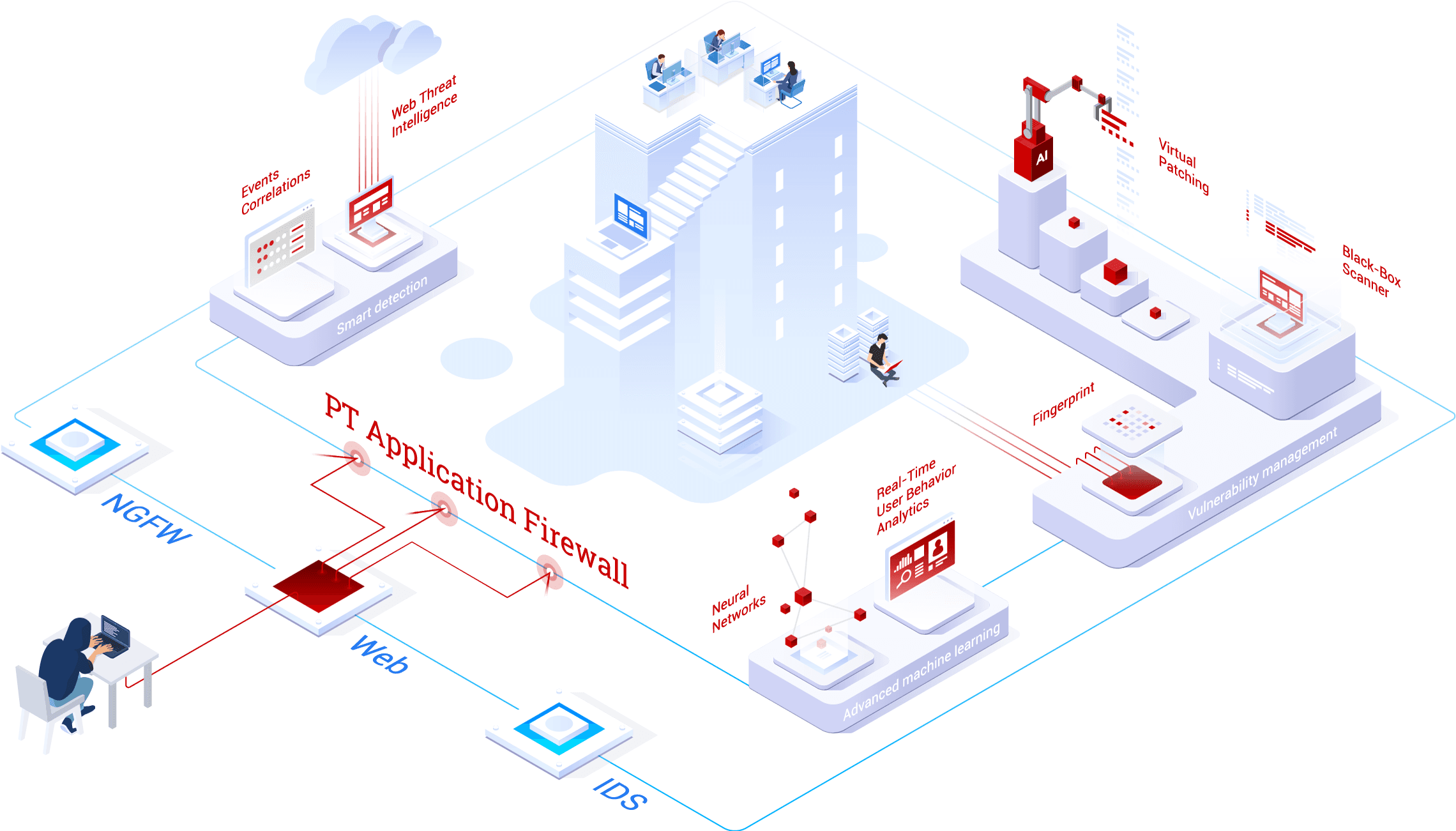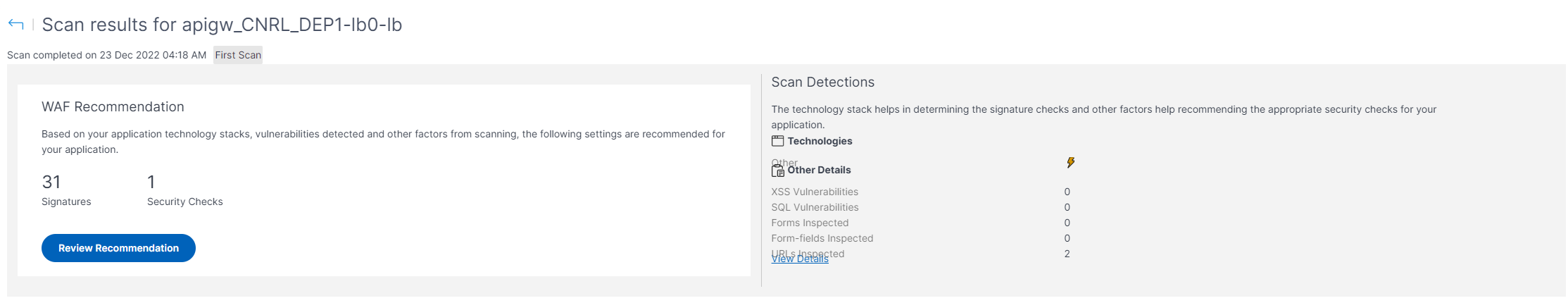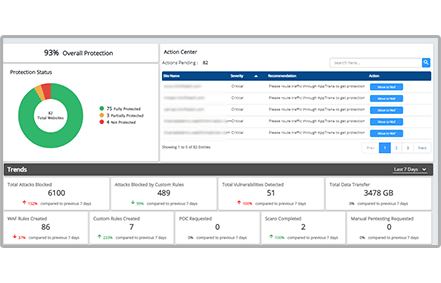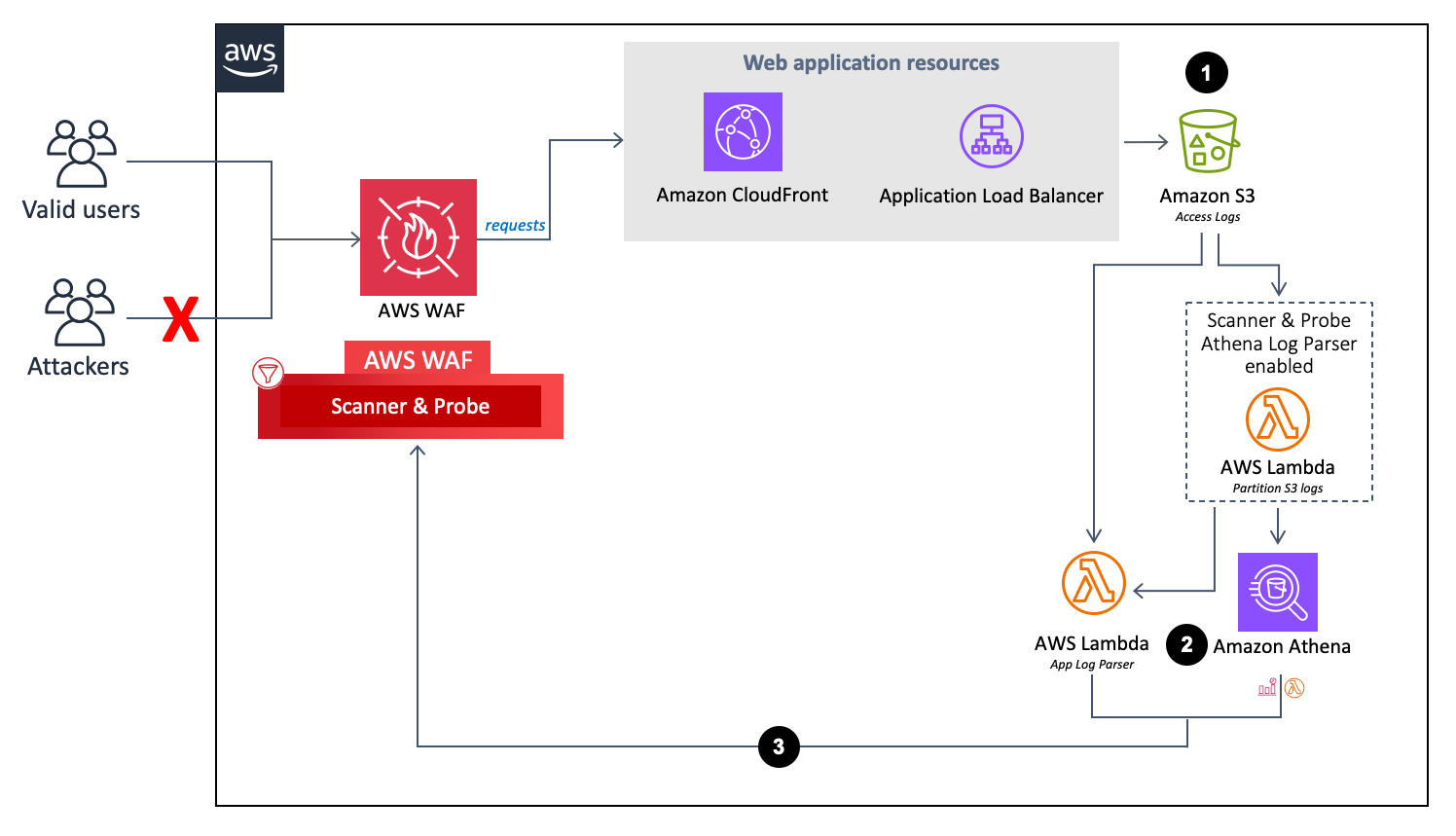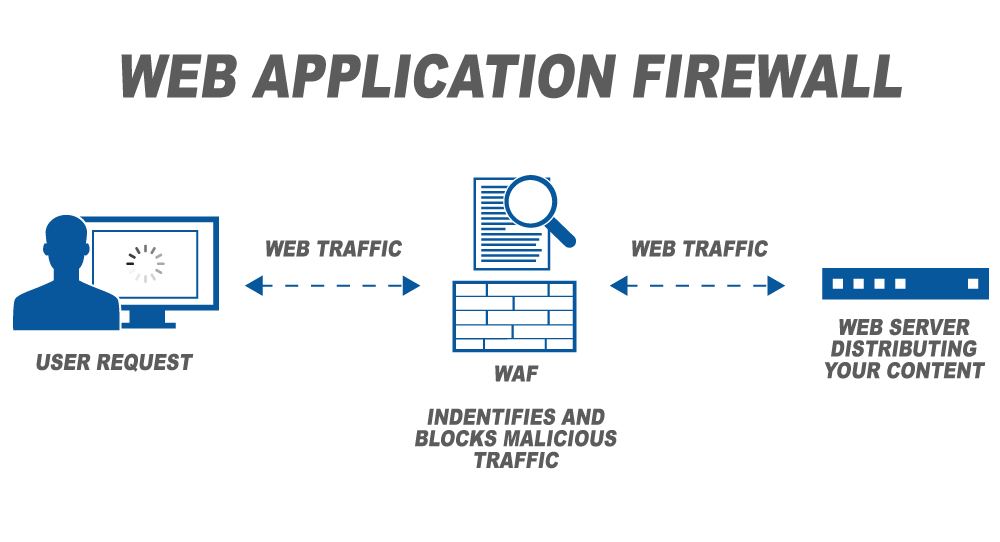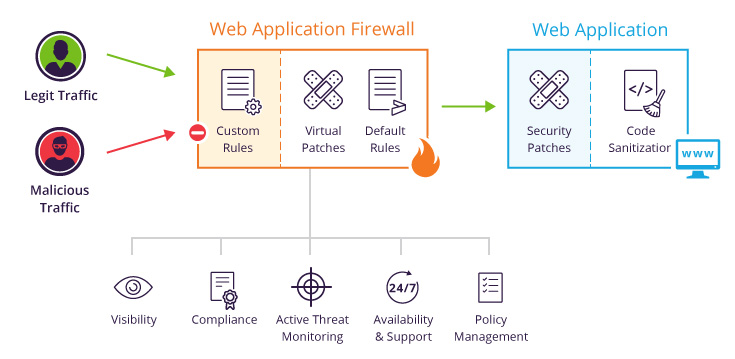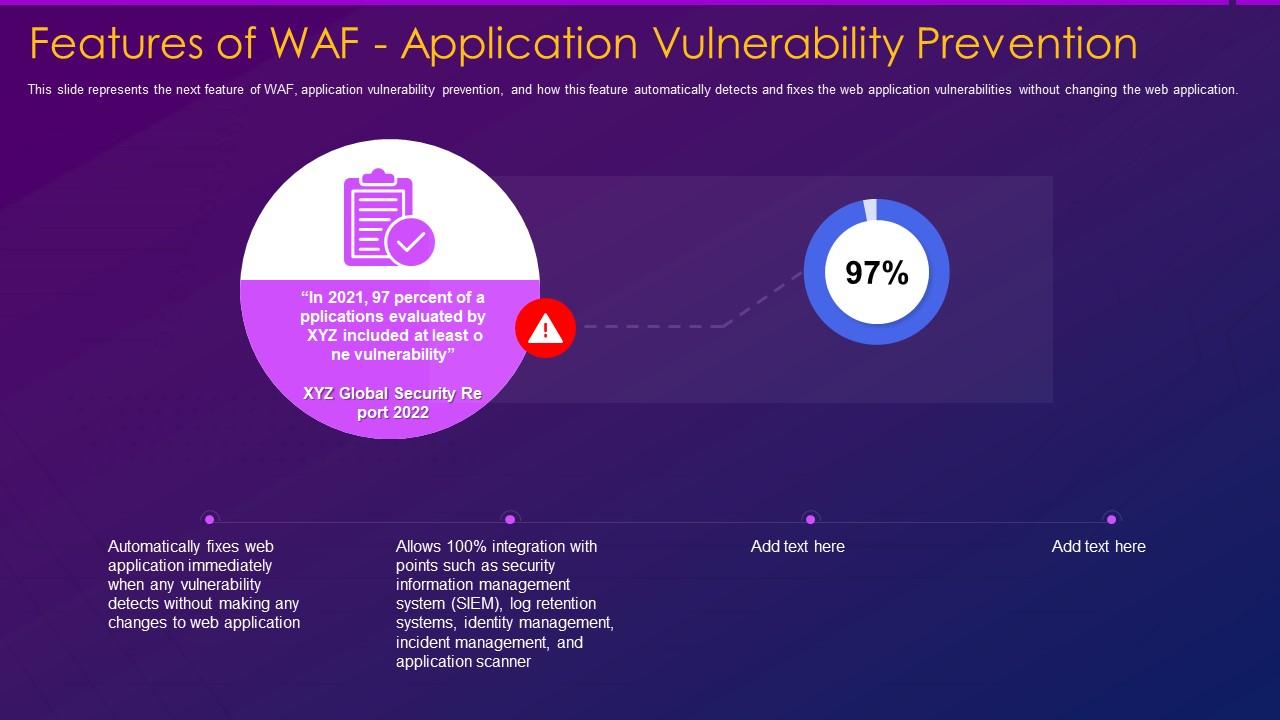
Features Of Waf Application Vulnerability Prevention Web Application Firewall Waf It | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
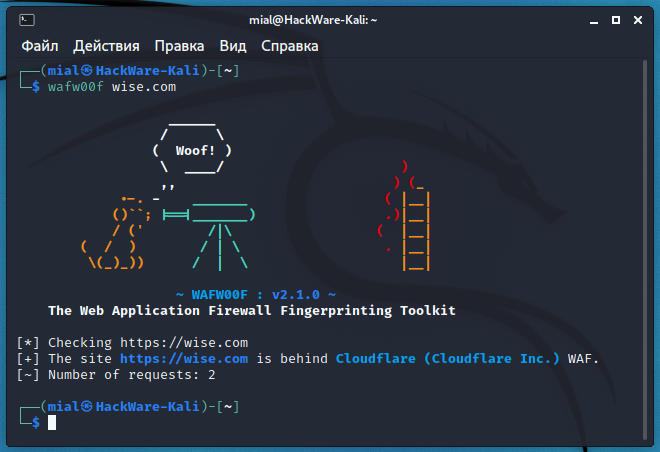
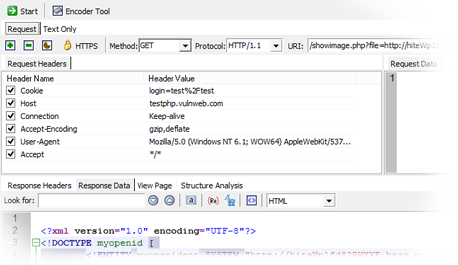
How to detect and identify the type of Web Application Firewall (WAF) - Ethical hacking and penetration testing